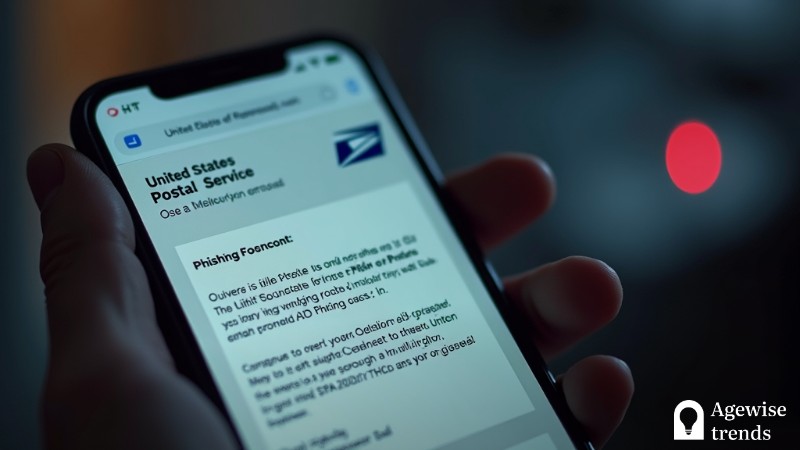
A new phishing campaign, targeting mobile users in over 50 countries, has been uncovered by cybersecurity researchers from Zimperium’s zLabs team. This large-scale attack, referred to as the “PDF Mishing Attack,” exploits the inherent trust users place in PDF files.
By embedding malicious links within these seemingly harmless documents, attackers lure victims to credential-stealing phishing websites. What makes this attack particularly concerning is its sophistication and ability to bypass traditional security systems, exposing a glaring vulnerability in mobile platforms.
The attack primarily masquerades as communications from reputable organizations, such as the United States Postal Service (USPS) and other trusted brands, increasing the likelihood of user engagement. With phishing now evolving to include multi-channel tactics, this campaign serves as a wake-up call for individuals and organizations alike to strengthen mobile security measures.
Key Takeaways
A new mobile threat, known as PDF Mishing Attack, is targeting users in over 50 countries by exploiting trust in PDF files to steal sensitive information.
- PDFs are being used as a medium for phishing attacks, with attackers embedding malicious links that bypass traditional security systems and target mobile devices.
- The attack primarily masquerades as communications from reputable organizations, increasing the likelihood of user engagement and making it harder to detect threats on mobile devices.
- To combat these threats, organizations must prioritize mobile security, adopt a layered defense strategy, and invest in user education, including recognizing suspicious links, verifying sender authenticity, and avoiding impulsive clicks on unverified content.
The exploitation of PDF trust
PDFs are widely regarded as secure and professional, making them a trusted medium for sharing sensitive information. They preserve formatting, include multimedia elements, and can even be digitally signed. However, this very trust has become their Achilles’ heel, as cybercriminals exploit it to deliver malicious content undetected.
According to Nico Chiaraviglio, Chief Scientist at Zimperium, “PDFs are integral to business communication due to their ability to maintain professionalism and integrity.” Cyber attackers have weaponized this trust by embedding phishing links in PDFs, which often escape traditional detection systems, particularly on mobile devices.
How the attack works
In this campaign, over 20 malicious PDFs and 630 phishing pages have been identified. The attackers embed phishing links within the PDFs, which, when clicked, redirect users to websites designed to steal sensitive information such as usernames, passwords, and financial details. Victims are led to believe these links are legitimate, often because the documents mimic official communications from entities like USPS, La Poste, and Deutsche Post.
Mobile devices are particularly vulnerable due to their smaller screens and limited interface, making it harder for users to scrutinize links or detect irregularities. Additionally, mobile devices often lack the robust security layers present on desktops, leaving users exposed to such sophisticated threats.
A growing threat across channels
Phishing attacks have evolved far beyond traditional email-based tactics. Today, attackers use multiple platforms, including SMS, messaging apps, and even social media, to reach their targets. Mobile users, in particular, are at higher risk due to their increasing reliance on these platforms for personal and professional communication.
Stephen Kowski, Field CTO at SlashNext, highlights the global nature of these attacks, stating, “Attackers are exploiting limited mobile security by impersonating trusted organizations like USPS, Royal Mail, La Poste, and Deutsche Post to target users worldwide.” This shift in strategy reflects a calculated effort to exploit the vulnerabilities of mobile platforms, which remain under-protected compared to traditional endpoints.
Advanced social engineering
The success of these phishing campaigns lies in their use of social engineering tactics. By mimicking official communications from recognizable brands, attackers manipulate victims into believing the messages are legitimate. This psychological approach exploits human trust, making it more likely for users to click on malicious links.
For instance, victims often receive PDFs that appear to be invoices, delivery notifications, or account statements. These documents are designed to look professional, further convincing users of their authenticity. The attackers also take advantage of urgency—such as claiming that a package delivery is pending or a payment is overdue—prompting users to act quickly without verifying the information.
The importance of mobile threat detection
The growing reliance on mobile devices for accessing sensitive data, such as banking information and work emails, has exposed a significant gap in traditional cybersecurity defenses. While desktop environments often benefit from advanced antivirus software and firewalls, mobile devices are frequently overlooked in security strategies.
Zimperium emphasizes the need for on-device threat detection, which can identify and neutralize threats directly on mobile devices before any harm is done. Such tools are essential for countering mobile-specific vulnerabilities, including limited user control and smaller screen sizes, which make detecting threats more challenging.
Emerging threats in PDFs
The threat landscape involving PDFs is expanding rapidly. Initially used as lures in phishing campaigns, PDFs are now being utilized to distribute advanced malware. For example, HP Wolf Security’s report highlights a surge in malware strains like WikiLoader, Ursnif, and DarkGate being delivered via PDFs. These malware types can infiltrate systems to steal data, record keystrokes, or even grant remote access to attackers.
This shift underscores the adaptability of cybercriminals and the urgent need for continuous improvements in security measures. Organizations must remain vigilant, as PDFs are no longer the “safe” files they were once thought to be.
Building a layered security framework
A well-informed user base is one of the strongest defenses against phishing attacks. Organizations must prioritize employee education to ensure users can identify and avoid phishing attempts. Training should include recognizing suspicious links, verifying sender authenticity, and avoiding impulsive clicks on unverified content.
Darren Guccione, CEO of Keeper Security, highlights the importance of awareness, stating, “Organizations must educate employees about phishing techniques and implement robust security frameworks to prevent unauthorized access.” Users should also be encouraged to confirm communications through official apps or websites, rather than relying on links provided in emails or PDFs.
Strengthening mobile defenses
To combat the rising threats against mobile devices, organizations should adopt a layered security strategy. Key measures include the following.
Real-time mobile threat detection: Mobile-specific security tools can detect and mitigate threats more effectively than traditional solutions.
Multi-Factor Authentication (MFA): Adding an extra layer of security ensures that compromised credentials alone cannot grant access.
Privileged Access Management (PAM): Restricting access to sensitive systems based on user roles minimizes potential damage.
Endpoint security solutions: Deploying solutions tailored for mobile platforms to ensure robust protection across all devices.
Regular updates: Keeping devices and apps updated with the latest security patches to mitigate known vulnerabilities.
Expanding protection beyond email
Organizations must address the security gaps in mobile and web messaging platforms. A comprehensive security strategy should encompass all communication channels, with a particular focus on safeguarding mobile devices. This requires significant investment in advanced security tools and fostering a culture of vigilance among employees.
Tackling PDF-based threats with technology
The escalating use of PDFs as a tool for cyberattacks necessitates innovative solutions. Emerging technologies like AI-driven threat detection and machine learning can analyze PDFs for malicious content in real-time. These tools are capable of identifying suspicious patterns, such as embedded links or unauthorized changes to the document’s metadata.
Organizations should also consider deploying sandboxing technologies, which isolate files in a controlled environment before allowing them to interact with a user’s system. This prevents malicious content from executing, even if the user interacts with the document.
The rise of the PDF Mishing Attack serves as a sobering reminder of the ever-evolving nature of cyber threats. By exploiting the trust users place in PDFs and leveraging sophisticated social engineering techniques, attackers have exposed a significant vulnerability in mobile platforms.
To combat these threats, organizations must prioritize mobile security, adopt a layered defense strategy, and invest in user education. Proactive measures, such as real-time threat detection, multi-factor authentication, and comprehensive mobile endpoint protection, are essential for mitigating these risks.
As the digital landscape continues to evolve, so too must security strategies. By addressing the vulnerabilities associated with mobile platforms and PDFs, organizations can reduce their risk exposure and safeguard sensitive information against the growing threat of multi-channel phishing attacks. In a world increasingly reliant on digital communication, vigilance and adaptability remain the cornerstones of effective cybersecurity.